We cannot deny the necessity of the Internet in both our personal and professional lives. With our increasing reliance on the internet, risks and the number of cybercriminals exploiting these vulnerabilities have also grown. Additionally, with the evolution of new programs and tools over time, activists can be exposed to hacking due to the nature of our work and/or the incorrect use of tools. So what’s the solution? Should we disconnect from the internet? Disconnecting from the internet in this age has become impossible!
Such a radical solution isn’t necessary, but we can educate ourselves and learn how to use the internet more safely. We may not be able to stop all hacking attempts, but we can mitigate them and reduce the potential harm caused in the case of a breach. Below, I have compiled a number of simple suggestions that will enhance your level of protection. These are relatively easy to implement – you do not need to be a cybersecurity expert! These measures include:
Protect Your Personal Information
We must protect ourselves from online fraud attempts by maintaining the confidentiality of personal details. For instance, avoid sharing phone numbers, social security numbers, national IDs, passport numbers, or banking information with unfamiliar individuals.
Create Complex/Strong Passwords
When creating passwords, it is best to include a mix of letters, numbers, and symbols:
- At least 8 characters long, preferably more than 14 characters.
- Special characters such as: -! @ # $ % ^ & * ().
- At least one uppercase and one lowercase letter.
- At least one number.
Following this method makes it difficult for hackers to breach our accounts. If you are not sure about the quality of your passwords, you can test them by using a tool such as the Kaspersky Password Checker. Additionally, we should avoid reusing the same password across all platforms. If a password is compromised or leaked on one account, all accounts using the same password become vulnerable to hacking.
These procedures help protect our passwords, however, it can become difficult for us to then track, remember, and input these passwords as needed. You might also consider using password management programs to create and track your passwords.
There are many free and paid programs available depending on the number of devices the tool is used on. Here are a few that I suggest:
Use Two-Factor Authentication (2FA)
Using 2FA enhances security by preventing others from accessing our accounts, even if they know the password. When this feature is activated, access to the account depends on two different authentication factors, typically a password and a verification code. There are many different authentication methods, but popular options include sending the verification code via the phone number or email associated with the account or through trusted devices we have previously registered.
Different websites and applications require or are compatible with different authentication methods. Usually, you can choose the most suitable method for you, whether you prefer receiving a text message by phone, receiving an email message, or downloading an authentication app like Google Authenticator, which generates these one-time use codes. In all cases where two-factor authentication is offered, we recommend that you activate this feature.
Always download updates from the official website or app store of the software or operating system. Avoid third-party websites or links shared through emails or messages, as they could be sources of malware.
It is safe to allow app permissions when you trust the app developer and understand why the app needs those permissions.
Verify the Reliability of Websites
Before making any purchases or entering our information into any website, we must ensure that it is secure. This can be done by checking for a small lock symbol or the letters “https” before the URL. (The URL is the address of a webpage that shows in your browser.) The “s” in “https” indicates “secure,” and the lock means that it has been confirmed as a secure site by our browser. Sometimes the browser may display differently on websites that are considered insecure, which we should not ignore when it appears on any website we want to browse. Insecure Website Secure Website


Regularly Update Your Operating System and Applications
The main reason developers of computer systems and software create updates is to protect users from security threats. Old software can contain bugs, vulnerabilities, and flaws that can be exploited by individuals who seek to infiltrate our devices and harm us. When developers become aware of these vulnerabilities, they create and release updates to fix the problems. Therefore, we must regularly and consistently update our systems from direct and reliable sources!
Monitor App Permissions When Downloading
We must familiarize ourselves with and monitor the privacy settings of any device, application, or service that we use. Some applications may require permission to access photos, microphones, cameras, or other personal information without our knowledge. We should always check the permissions we grant to applications when downloading them to avoid sharing any information we do not wish to share.
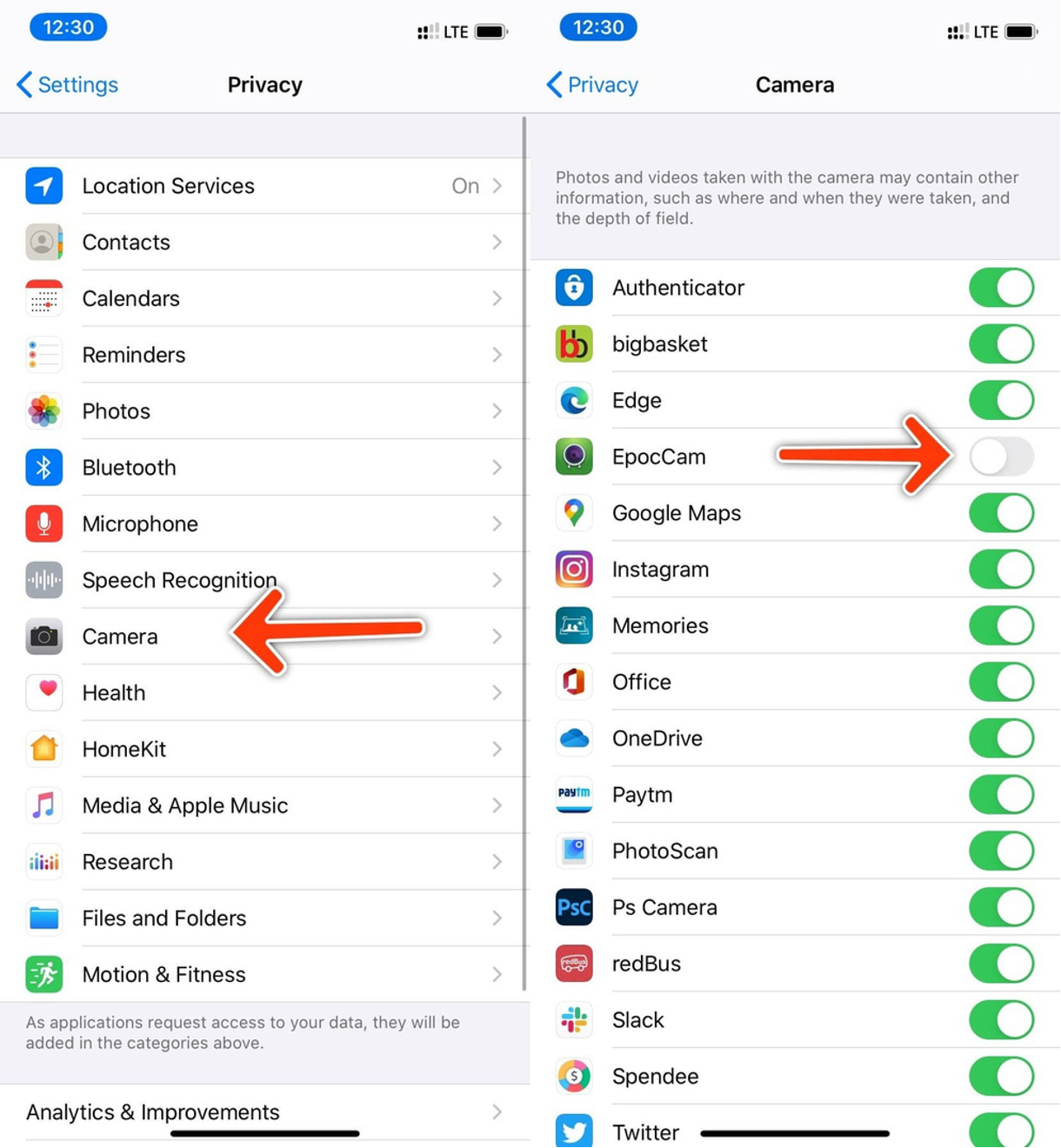
Here you can see that I’ve allowed many apps access to my mobile camera, but have turned off permission for EpocCam.
Be cautious when using public Wi-Fi networks
We often need access to the Internet outside our homes or workplaces, which means that we may have to connect to public Wi-Fi networks such as airports, restaurants, and hotels. However, connecting to these networks can be dangerous because using unsecured networks exposes us to receiving harmful software and vulnerable to bad actors accessing our personal information.
The internet represents a vital part of our daily lives, offering us immense opportunities and positive transformations. However, we should not ignore the challenges and risks we may face while accessing this digital world. By adopting appropriate security measures, we can reduce risks and protect our privacy online.
I encourage you to embrace safe online behaviors and seek to educate yourself on the latest ways to protect ourselves and our information. Thanks to advanced technologies and continuous awareness, we can enjoy the benefits of the internet safely and effectively, achieving a crucial balance between leveraging technology and maintaining our personal security and digital stability.
This perspective was contributed by Ayman Malhis, New Tactics in Human Rights MENA Digital Media Senior Coordinator.